The PE Entry Point
Important notes
- It can be confusing when the debugger breaks on the PE entry point only to find some code that is not related to the main functionality of the binary.
- This code is inserted automatically by the MSVC compiler.
MSVC Console Application Entry Point
- The entry point serves two purposes, it calls the
__security_init_cookiefunction then jumps to the__scrt_common_main_sehthunk. - The
__scrt_common_main_sehthunk then performs some setup for the binary including structured exception handler (SEH) before callingmain.
__security_init_cookie (buffer overflow protection)
- The
__security_init_cookiefunction is a pattern that is important to recognize as a pattern, as it can be used to “localize” ourselves if we are looking at PE file in memory. The purpose of the cookie is to initialize the global security cookie. (Buffer overflow protection)
__scrt_common_main_seh (identifying main)
- The
__scrt_common_main_sehthunk is used to setup some SEH related stuff for the binary and then call intomain. - It can be confusing to identify where main is without labels inside x64dbg. Luckily MSVC console applications all have the same main function prototype.
1
main(int argc, const char **argv, const char **envp)
- The function prototype can be used to identify the call to main in
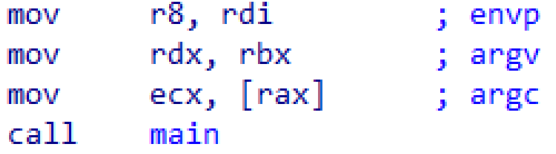
scrt_common_main_seh, simply by looking for three arguments that are passed to main includingargc,argv,envp. In 64-bit binaries these arguments are compiled into a serious of threemovinstructions, moving the arguments into the registers RCX, RDX, R8:
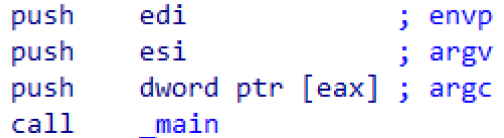
- In 32-bit binaries these arguments are compiled into a series of three
pushinstructions pushing the arguments onto the stack.
This post is licensed under
CC BY 4.0
by the author.